hold data and code confidential Implement policy enforcement with encrypted contracts or protected enclaves in the mean time of deployment to ensure that your data and code is not altered Anytime.
Anti-funds laundering/Fraud detection. Confidential AI will allow multiple financial institutions to combine datasets within the cloud for training much more precise AML designs without having exposing personalized data of their buyers.
Providing the right treatment in your tees will help continue to keep them seeking sharp and emotion cozy for eons. 1st up, go through the damn label! Make sure you Adhere to the Recommendations. Also, be sure to independent shades whenever you wash t-shirts—darks with darks and lights with lights.
from the rapidly-paced and at any time-evolving landscape of synthetic intelligence, a fresh drive is making its existence felt—Safe Superintelligence (SSI). Co-Started by previous OpenAI chief scientist Ilya Sutskever, SSI has speedily captured notice by elevating over $1 billion in cash from well known traders.
Confidential computing engineering isolates sensitive data inside a protected CPU enclave in the course of processing. The contents of your enclave, which involve the data currently being processed as well as techniques which can be accustomed to process it, are obtainable only to authorized programming codes. They're invisible and unknowable to everything or everyone else, such as the cloud supplier.
The purchase has provisions for preserving Us citizens’ privacy, although it acknowledges that the opportunity to do so is proscribed without having a federal data privacy law and phone calls on Congress read more to pass 1.
the same as Intel SGX virtual machines, container purposes which are created to run in enclaves have two elements:
Regardless of the very affordable selling price, this felt about as elevated for a t-shirt will get. The pima cotton, which is made of excess very long fibers that make for a softer really feel and smoother seem, has an expensive physical appearance. What's more, it manufactured for a really comfortable undershirt that didn’t add any bulk when layering.
Don’t contain individual or economic info like your National insurance plan variety or charge card specifics.
When Azure confidential computing is enabled and effectively configured, Microsoft is unable to accessibility unencrypted shopper data.
This can be attained in Azure employing a components root of trust not controlled by the cloud provider, which is intended to ensure unauthorized accessibility or modification in the natural environment.
you will discover security fears close to hugely sensitive data, and many kinds of data, like wellbeing care details, frequently has polices close to how it might be taken care of.
Their leadership implies a investigate-major method aimed at resolving complex problems in AI safety, as opposed to purely business ventures.
Beach or vacation resort: Style a light-weight and breezy t-shirt with swim trunks or linen shorts for your beach-All set glance. Wear flip-flops or sandals to enhance the trip vibe.
 Dylan and Cole Sprouse Then & Now!
Dylan and Cole Sprouse Then & Now!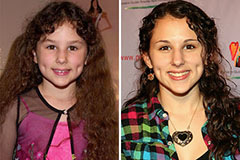 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Richard "Little Hercules" Sandrak Then & Now!
Richard "Little Hercules" Sandrak Then & Now! Tahj Mowry Then & Now!
Tahj Mowry Then & Now! Andrew Keegan Then & Now!
Andrew Keegan Then & Now!